Appearance
KUDO ID™ - DID Module of IOST 3.0
KUDO ID™ (Know Ur Digital Ownership) is a next-generation, decentralized biometric identity protocol designed for secure authentication, payments, and decentralized identity (DID) verification. By leveraging dual-modal palm vein and palm print biometrics, KUDO ID™ delivers fraud-resistant, privacy-preserving digital identity solutions that integrate seamlessly across Web2, Web3, and DeFi ecosystems.
The rise of fake identities (52.5 to 150 billion accounts) and automated bot-driven fraud (90% of stablecoin transactions, 90% of airdrops targeted by Sybil attacks) has created a $1 trillion risk in digital finance. KUDO ID™ mitigates these risks by employing zero-knowledge proof (ZKP) cryptography, allowing users to verify their identity without exposing sensitive data on IOST.
Core Advantages
- 99.9% biometric accuracy, reducing false acceptance rates (FAR < 0.01%)
- Multi-chain interoperability with BNB Chain and IOST, ensuring scalability and high-speed, low-cost identity verification
- Decentralized Identity (DID) + Palm-Based Payments, enabling frictionless financial transactions while maintaining full user control
- GDPR & CCPA Compliance with self-sovereign identity (SSI) architecture, ensuring regulatory trust and privacy
- Tokenized incentives & staking, where verified users and ecosystem participants earn rewards for securing the network
By 2028, over 1 billion users are projected to need decentralized identity solutions, making KUDO ID™ a fundamental infrastructure module for IOST expansion to Web3 finance and payments.
1. System Architecture
Biometric Data Capture and Processing
- Dual-Modal Biometric Identification: KUDO ID™ leverages dual-modal biometric recognition, capturing both palm vein and palm print data for maximum security.
- Image Capture Devices: The system uses RGB/IR cameras to acquire high-resolution palm vein and print data.
- Preprocessing Techniques:
- Grayscale Conversion
- Denoising and Enhancement
- Region of Interest (ROI) Extraction
- Segmentation of biometric patterns (e.g., skin lines, whorls)
Feature Extraction and Matching
- Feature Extraction: Core attributes (e.g., texture, vein patterns) are encoded into vectors through advanced algorithms.
- Feature Matching: Using Euclidean Distance, Correlation Coefficient, and deep learning matching algorithms, the system verifies identity with high precision.
Decentralized Storage and Privacy Control
- Zero-Knowledge Proof (ZKP): ZKP technology enables users to prove identity without revealing biometric data, protecting user privacy.
- Decentralized Ledger: Each verified user's ID (DID) and verifiable credentials (VC) are securely stored on-chain, providing immutability and transparency.
- User-Controlled Data: Data is stored in a decentralized manner, with users maintaining ownership and access rights through self-sovereign identity (SSI).
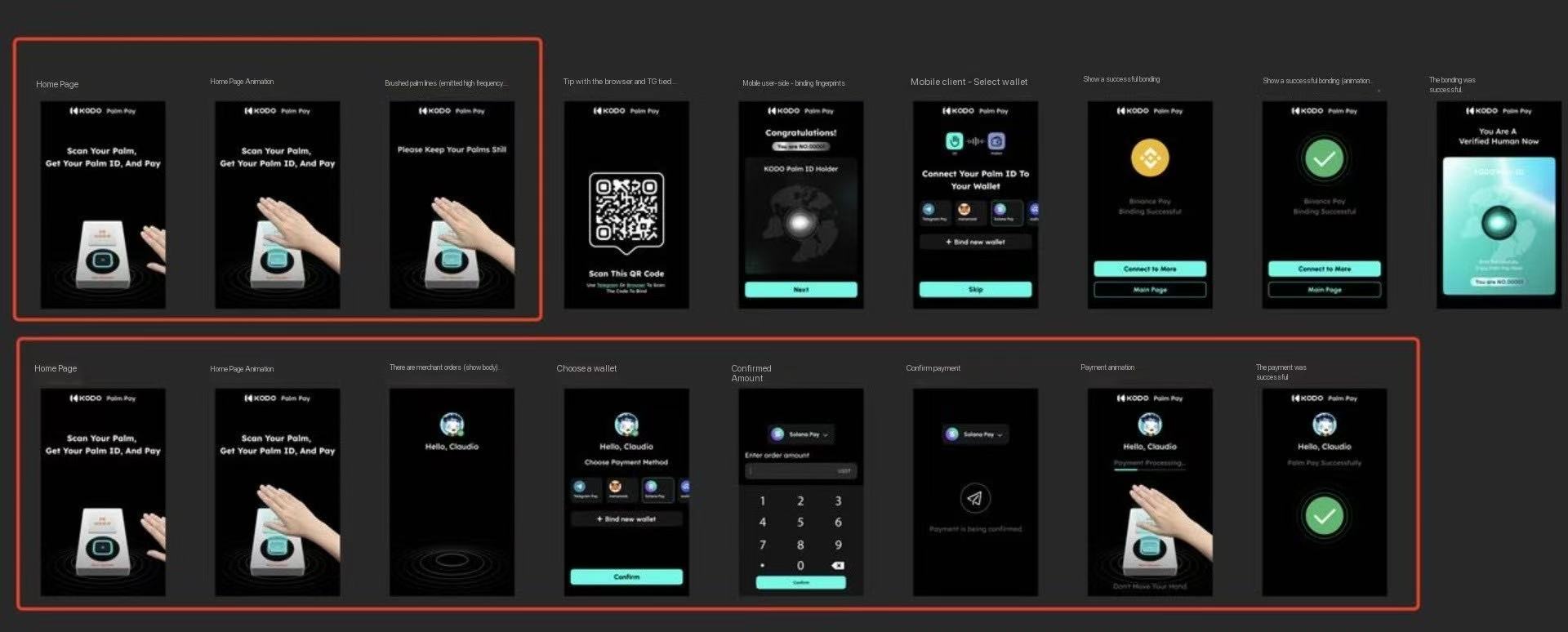
2. Security and Privacy
Multi-Layered Authentication Protocols
- Biometric Matching Accuracy: The system is optimized to minimize False Acceptance Rate (FAR) and False Rejection Rate (FRR) by setting precise thresholds for identity confirmation.
- Zero-Knowledge Proof Integration: Allows the system to confirm identity without exposing personal data, using cryptographic proofs.
Compliance with Global Standards
- GDPR/CCPA Compliance: KUDO ID™ is designed to meet stringent global privacy regulations, ensuring user data control and informed consent.
- Decentralized Identity Verification: Ensures compliance by limiting access to verified users only and maintaining secure data control on-chain.
3. Technological Innovation
| Feature | Description |
|---|---|
| Dual-Modal Biometrics | Combines palm vein and print data for accurate and secure identification |
| Zero-Knowledge Proof | Proves identity without disclosing sensitive data |
| Decentralized Storage | Stores IDs and verifiable credentials on-chain, ensuring immutability and user control |
| Web2 and Web3 Integration | Enables seamless interoperability between traditional and decentralized systems |

4. Payment Utilization & Infrastructure
- How KUDO ID™ enables biometric transactions via BNB Chain (scalability) & IOST (high-speed, low-cost processing)
- Integration with DeFi protocols for instant loan approvals based on verified identity
- Biometric-backed crypto payments, reducing fraud in e-commerce and remittances
5. Future Roadmap
| Milestone | Description | Target Date |
|---|---|---|
| Beta Testing on IOST | Initial testing of KUDO ID™ on the IOST network to assess scalability | Q1 2025 |
| Multi-Chain Expansion | Integrate with other blockchains for broader compatibility | Q3 2025 |
| Enhanced Compliance Features | Develop additional compliance tools for evolving global regulations | Q4 2025 |
| Expanded Use Cases | Explore more applications in finance, healthcare, and e-commerce | 2026 |
6. Data Flow Architecture
Data Capture and Encryption Process
This flow ensures secure capture, encryption, and storage of biometric data.
| Step | Description |
|---|---|
| Capture | RGB/IR cameras capture high-resolution palm vein and print data |
| Preprocessing | Data is denoised, enhanced, and segmented to extract core biometric features |
| Feature Encoding | Biometric features are encoded into vectors for analysis |
| Zero-Knowledge Proof | Biometric data verified without exposure to third parties |
| Decentralized Storage | Data is stored on-chain, with control retained by the user |
7. Biometric Security Comparisons
To underscore the security of KUDO Palm ID, here's a table comparing various biometric security types:
| Biometric Type | Uniqueness | Difficulty to Replicate | Privacy Risk |
|---|---|---|---|
| Palm Print | High | Difficult | Low |
| Palm Vein | Very High | Extremely Difficult | Very Low |
| Iris | Very High | Moderate | Moderate |
| Fingerprint | Moderate | Moderate | High |
| Facial Recognition | Low | Easy | High |
KUDO Palm ID leverages palm vein and print recognition, maximizing security and minimizing privacy risks.
8. Compliance and Privacy Standards
Compliance by Design
KUDO ID™ aligns with global standards, ensuring user data sovereignty and privacy.
| Compliance Standard | KUDO ID™ Approach |
|---|---|
| GDPR | User-controlled data storage; transparent consent process |
| CCPA | Right to privacy embedded with zero-knowledge proofs |
| ISO 27001 | Secure data management practices with decentralized storage |
| AML/KYC Integration | Option for regulated entities to access verified identities without compromising user privacy |
Zero-Knowledge Proof in Compliance
Zero-Knowledge Proofs enable user verification without disclosing data to third parties, ensuring data remains private while still compliant with regulatory requirements.
9. Competitive Landscape
| Solution | Key Features | Privacy Model | Market Fit (Web2/Web3) |
|---|---|---|---|
| KUDO Palm ID | Palm vein/print, decentralized, ZKP | Full user control | Web2 and Web3 |
| Worldcoin | Iris scan, centralized storage | Centralized | Web3 |
| Apple FaceID | Facial recognition, device-based | Device storage | Web2 |
| Polygon ID | Digital ID, decentralized | User-controlled | Web3 |
KUDO Palm ID is uniquely positioned with its dual-modal biometrics and privacy-first design, making it suitable for both Web2 and Web3 payment applications.
Conclusion
KUDO ID™ represents a significant advancement in decentralized digital identity by providing a secure, user-controlled, and globally compliant biometric solution on IOST 3.0. Its integration of dual-modal biometrics, zero-knowledge proofs, and decentralized governance positions KUDO ID™ as a groundbreaking technology.
