Appearance
DID for RWA
IOST 3.0's decentralized identity framework provides the essential trust layer for real-world asset (RWA) tokenization, enabling compliant, transparent, and secure asset representation on blockchain.
Integration Overview
The integration of DID with the RWA framework creates a seamless connection between digital identity and tokenized assets:
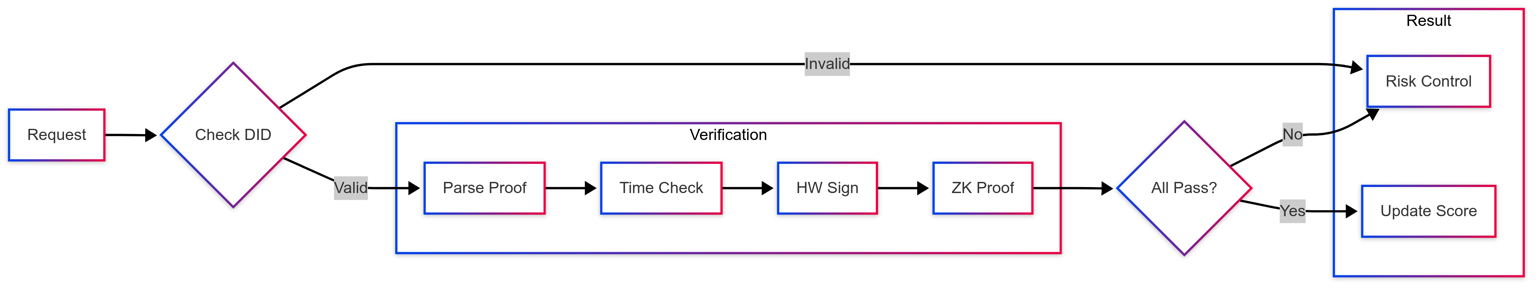
RWA Tokenization Flow
This diagram illustrates how DID serves as the trust layer throughout the RWA tokenization lifecycle, enabling secure identity verification and regulatory compliance at each step of the process.
Core Integration Points
DID forms the foundation of trust for RWA through several critical integration points:
Identity Verification: Linking real-world identities to digital asset ownership
Compliance Framework: Enforcing regulatory requirements throughout the asset lifecycle
Access Control: Managing permissions for asset operations based on identity attributes
Audit Trail: Creating verifiable records of all asset-related activities
Regulatory Compliance
DID enables comprehensive regulatory compliance for tokenized assets:
KYC/AML Integration
The framework provides multiple verification levels to satisfy regulatory requirements:
| Verification Level | Requirements | Asset Access |
|---|---|---|
| Basic | ID verification, risk screening | Low-value assets |
| Enhanced | Address verification, source of funds | Intermediate assets |
| Advanced | Biometric verification, advanced due diligence | High-value assets |
| Institutional | Corporate documentation, beneficial owner verification | Institutional-grade assets |
Compliance Credentials
IOST 3.0 implements specialized verifiable credentials for RWA compliance:
Investor Accreditation: Verifies qualified investor status
Jurisdictional Eligibility: Confirms legal eligibility in specific regions
Suitability Assessment: Documents appropriate investment suitability
Sanctions Screening: Verifies absence from global sanctions lists
Transfer Restrictions
DID-based transfer controls enforce ownership restrictions:
Rule-based Transfers: Programmatic enforcement of transfer rules
Holding Periods: Automated lock-up period enforcement
Ownership Concentration Limits: Prevention of excessive ownership concentration
Jurisdictional Controls: Geographic restrictions on asset transfers
Asset Authentication
DID provides critical infrastructure for authenticating real-world assets:
Asset Provenance
Verifiable credentials document asset history and authenticity:
Origin Verification: Documenting authentic asset creation or issuance
Chain of Custody: Tracking ownership changes through verifiable credentials
Condition Assessment: Verified reporting of asset condition and status
Valuation Credentials: Trusted third-party valuations with verifiable credentials
Real-World Verification
Connecting physical assets to digital tokens through:
Physical Identifiers: Linking unique physical properties to digital identifiers
Verification Oracle Network: Decentralized real-world verification services
Location Attestations: Secure verification of asset geographic location
Sensor Integration: IoT connectivity for real-time asset monitoring
Privacy-Preserving Ownership
DID enables confidential ownership while maintaining regulatory compliance:
Selective Disclosure
Asset owners can selectively disclose ownership details:
Minimal Disclosure Proofs: Verifying ownership status without revealing identity
Threshold Disclosures: Progressive information revelation based on need
Anonymous Ownership: Privacy-preserving ownership with regulatory backdoors
Zero-Knowledge Compliance: Proving regulatory compliance without data exposure
Confidential Transactions
Privacy-preserving transaction mechanisms:
Shielded Transfers: Confidential ownership transfers with selective visibility
Private Metadata: Encrypted asset details accessible only to authorized parties
Auditable Privacy: Maintaining privacy while enabling regulatory oversight
Security Model
DID provides robust security for RWA tokenization:
Multi-Party Authorization
Critical asset operations require multi-signature approvals:
Custody Solutions: Institutional-grade asset custody with distributed control
Governance Controls: Multi-stakeholder oversight of significant asset actions
Threshold Signatures: M-of-N approval requirements for high-value operations
Access Revocation
Mechanisms to handle lost keys or compromised accounts:
Emergency Freeze: Temporary suspension of asset operations
Graduated Recovery: Progressive recovery options based on verification level
Regulatory Intervention: Compliant mechanisms for legal enforcement actions
Proof of Heartbeat:Hardware-based PoH
The Proof of Heartbeat (PoH) mechanism represents a revolutionary advancement in decentralized identity verification, combining biometric behavioral analysis with on-chain dynamic validation to create an unforgeable digital identity system.
Technical Positioning & Core Value
PoH is an innovative identity verification protocol within the IOST ecosystem designed to address three fundamental challenges in traditional blockchain systems:
Identity Uniqueness Guarantee: Ensures each decentralized identity (DID) corresponds to a unique real individual by fusing multimodal biometric data (heart rate patterns, gesture characteristics) with hardware fingerprinting.
Continuous Compliance Monitoring: Verifies user identity vitality in real-time during payment and financial transaction scenarios, dynamically adjusting credit limits and operational permissions.
Privacy-Enhanced Design: Employs zero-knowledge proof technology to verify identity without exposing any original biometric data, achieving "verifiable but unknowable" privacy protection.
Technical Implementation Framework
Biometric Feature Collection
Multi-Sensor Coordination:
- Optical Sensors: Capture subcutaneous blood flow characteristics using green LED and photodiodes, generating Heart Rate Variability (HRV) waveforms
- Capacitive Sensors: Detect finger contact patterns during natural operations (pressing force, sliding trajectories)
- Motion Sensors: Capture device micro-vibration characteristics to distinguish real human behavior from mechanical imitation
Dynamic Feature Fusion Algorithm:
Sensor data undergoes encrypted processing within the secure element:
Raw Data -> Spatiotemporal Alignment -> Feature Extraction -> Hash Obfuscation -> Zero-knowledge commitmentsGenerating irreversible compound biometric hash values that ensure original data never leaves the device.
On-Chain Verification Mechanism
- Vitality Proof Generation:
During each identity verification, the device generates an encrypted proof package containing:
- Timestamp encrypted digest
- Biometric feature hash commitment
- Hardware unique identifier
- Zero-knowledge proof signature
- Smart Contract Verification Process:
Credit Model Construction
The system builds a dynamic credit system based on continuous verification records:
Rating Score = Base Score × log (number of consecutive active days) Number of anomalies × Risk factorwith scoring results directly affecting:
- Single transaction limits
- Cross-chain operation permissions
- Governance voting weight
RWA Integration Applications
PoH significantly enhances the security and compliance of RWA operations:
- Asset Anchoring Verification:
- Issuers must pass Proof of Heartbeat verification to ensure legal binding between physical assets and on-chain DIDs
- Creates unforgeable links between real-world asset controllers and their digital representations
- Prevents unauthorized asset tokenization through biometric verification checkpoints
- Investor Access Control:
- Implements tiered access controls based on biometric verification levels
- Enables continuous compliance monitoring for high-value asset transactions
- Authorizes major asset operations only with live biometric verification
- Advanced Sybil Attack Prevention:
- Hardware-based biometric verification makes creating multiple fake identities prohibitively difficult
- Continuous validation prevents account takeovers after initial verification
- Creates an unparalleled security layer for high-value RWA management
- Dynamic Transaction Authorization:
- Transaction permissions adjust based on real-time biometric verification confidence scores
- Implements step-up authentication for transactions above certain thresholds
- Provides additional security layer for high-value asset transfers and conversions
The integration of Proof of Heartbeat with DID for RWA represents a significant advancement in blockchain identity security, creating a foundation of trust that is essential for institutional-grade asset tokenization.
Asset Lifecycle Management
DID facilitates complete asset lifecycle management:
Issuance & Origination
The process of creating compliant tokenized assets:
Issuer Verification: Comprehensive verification of asset originators
Asset Documentation: Structured recording of all relevant asset information
Compliance Configuration: Setting up appropriate regulatory parameters
Distribution Controls: Implementing compliant distribution mechanisms
Servicing & Dividends
Ongoing asset management operations:
Income Distribution: Privacy-preserving dividend and interest payments
Voting Rights: Secure, verifiable governance participation
Corporate Actions: Management of splits, mergers, and other corporate events
Retirement & Exchange
End-of-life asset operations:
Redemption Verification: Identity-verified asset redemption processes
Asset Transformation: Compliant conversion between asset types
Secondary Market Controls: Maintaining compliance in secondary trading
Use Cases
The integration of DID and RWA enables powerful use cases:
Real Estate Tokenization
Property Title Verification: Digital verification of legal ownership
Fractional Ownership: Compliant partial property ownership
Rental Income Distribution: Automated and verified income sharing
Cross-Border Investments: Compliant international real estate investment
Financial Instruments
Bond Issuance: Compliant debt instrument tokenization
Equity Securities: Tokenized company ownership with governance rights
Syndicated Loans: Multi-party financing with on-chain compliance
Structured Products: Complex financial products with built-in compliance
Luxury Assets
Art Provenance: Verified ownership history and authenticity
Collectibles Authentication: Verified authenticity and condition assessment
Fractional Collections: Compliant shared ownership of high-value items
Insurance Integration: Automated coverage verification and claims
Related Components
DID for RWA connects with other IOST 3.0 modules:
- DID on Layer 2: Scalable identity for high-volume asset operations
- DID in Payment Solutions: Secure transactions for asset trading
- Trust Framework: Governance rules for asset verification
