Appearance
KYC/KYB & AML Module
Overview
In Real World Asset (RWA) trading scenarios, all participants—including individual investors, institutional investors, and the platform itself—undergo rigorous compliance review to ensure that:
- Buyer identity is legitimate: The system confirms that users are who they claim to be.
- Funding sources are compliant: Transaction funds are verified to be legal and properly sourced.
- Trading behavior complies with legal and regulatory standards: All transactions adhere to established regulations.
Within the IOST technology stack, we deploy a dedicated KYC/KYB/AML module. This module integrates third-party services, including Persona for identity verification, Elliptic for blockchain-based AML monitoring, and a specialized KYB partner for business verification. This integration ensures data authenticity, integrity, and traceability.
Module Function Overview
KYC
Persona is the third-party solution for KYC verification. It provides:
- Identity Verification: It validates identity documents (ID cards, passports, and driver’s licenses) and performs liveness checks to confirm that the user’s submitted identity matches their true identity.
- User Information Management: It securely encrypts and stores personal details including name, address, date of birth, and nationality.
- Risk Rating: It assigns a risk score based on factors like document authenticity, age, and regional risk, ensuring a precise basis for compliance decisions.
KYB
Trulioo serves as our dedicated KYB solution for verifying business entities. It provides:
- Corporate Registration Verification: It verifies a company’s legal registration, licenses, and official documents.
- Ownership and Management Verification: It confirms the identities of directors, ultimate beneficial owners (UBOs), and other key stakeholders.
- Operational and Financial Risk Assessment: It evaluates business credibility, financial health, and any risk indicators to ensure compliance with regulatory requirements.
AML
Elliptic & Chainalysis deliver blockchain-based AML and compliance monitoring:
- Blockchain Address Monitoring: It assesses wallet addresses for connections to illicit funds, hacking activity, or sanctioned entities.
- Transaction Tracing: It monitors on-chain fund flows and detects suspicious patterns with precise alerts for immediate action.
- Compliance Reporting: It generates regulatory-compliant reports that support audits and detailed analysis by compliance teams.
Technical Architecture
Module Interaction
1. User Interface
- Individuals and institutions submit their KYC/KYB documentation and wallet addresses through a secure frontend.
- Users initiate transactions on-chain.
2. KYC Module (Persona) & KYB Module (Trulioo)
- The system receives user and business data and sends it to the respective third-party services using secure APIs.
- Persona returns a KYC report, and Trulioo provides a KYB report with all necessary verification details.
3. Compliance Decision (Asset Issuer)
- The asset issuer reviews the KYC and KYB reports alongside AML data to determine compliance status.
- The compliance decision is based on internal standards and regulatory requirements for RWA trading.
4. AML Module (Elliptic)
- The system submits wallet addresses to Elliptic, which analyzes them for risk and produces an AML report.
- The AML results further support the final compliance decision.
5. Business Contract (IOST L2 Chain)
- The smart contract verifies the stored compliance status before permitting asset transactions.
- It records compliance changes or verification results as hashes or summarized data to protect sensitive information.
Workflow
A typical end-to-end process combining KYC, KYB, and AML functions is as follows: 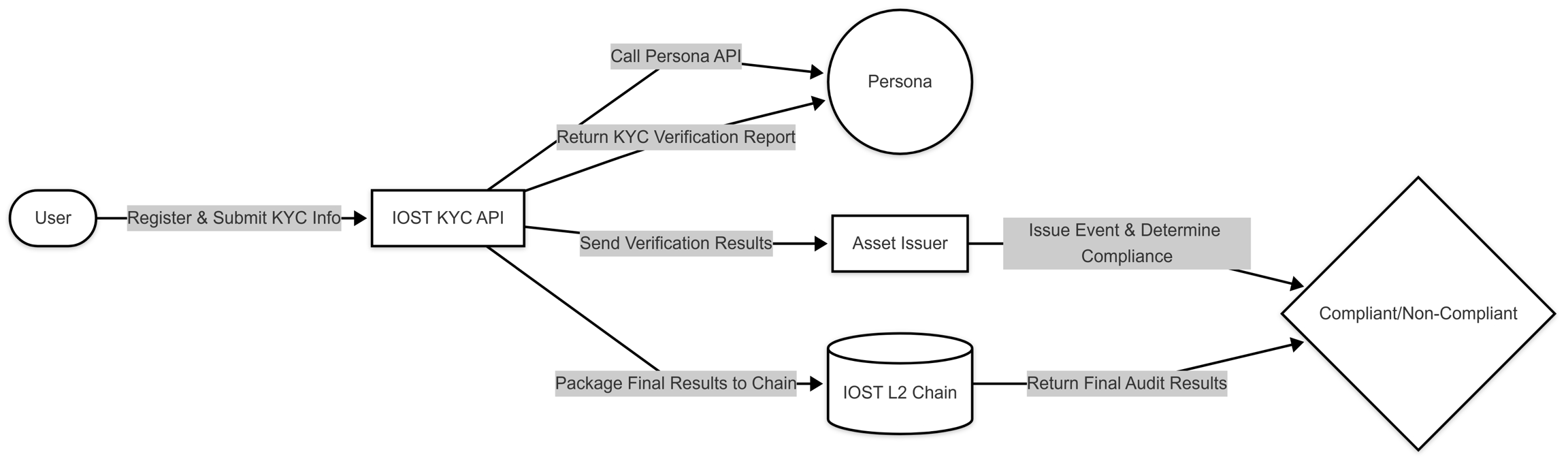 Open toolbar Compliance Module
Open toolbar Compliance Module
1. Registration and Submission
- Personal users submit their identification documents, while business entities submit corporate registration and ownership data.
2. Verification via Third-Party Services
- Persona validates individual identity and issues a KYC report.
- Trulioo verifies business credentials and issues a KYB report.
- Elliptic monitors wallet addresses and produces an AML report.
3. Compilation of Compliance Report
- The asset issuer reviews all reports and determines the compliance status, categorizing users as “Compliant,” “Non-Compliant,” or “Requires Further Review.”
4. On-Chain Recording
- The final compliance decision is recorded on the IOST L2 Chain as a hashed or summarized record to secure data integrity and privacy.
Data Handling and Storage
Data Classification
- Personal/Corporate Information: Stored within Persona, Trulioo, and the platform’s internal compliance databases. This includes names, identification numbers, addresses, and corporate registration details.
- On-Chain Transaction Data: Includes immutable records of transactions and smart contract interactions on the IOST L2 Chain.
- Compliance Status: The final KYC/KYB/AML results are stored on-chain as hashed records or summarized status flags.
- Logs and Audit Data: All API interactions and verification processes are securely logged for audit and compliance reviews.
Data Security and Privacy
- Encrypted Storage: Sensitive data is encrypted using AES-256 and stored in secure databases or encrypted file systems.
- Secure Transmission: All communications with third-party APIs are transmitted over HTTPS/TLS.
- Access Controls: RBAC and IAM systems enforce least-privilege access, ensuring that only authorized personnel view full data details.
- Audit Logging: Every access and modification to sensitive data is logged with timestamps, user identifiers, and justifications, with periodic reviews conducted.
Security and Privacy Design
- Encryption and Digital Signatures: All KYC, KYB, and AML reports are stored using robust encryption and digital signatures to prevent tampering and unauthorized disclosure.
- Data Minimization: Only essential compliance summaries and hashed references are recorded on-chain, ensuring that no sensitive personal or corporate data is directly exposed.
- Strict Access Control: Sensitive records are accessible only to designated compliance personnel or automated systems, while public blockchain data displays only non-sensitive status flags and hash pointers.
RWA Application Scenarios
This compliance module supports a wide range of RWA trading scenarios:
- Tokenized Real Estate: Verifies individual buyers and corporate investors to comply with real estate regulations and prevent fraudulent transactions.
- Supply Chain Finance: Confirms that all participating businesses meet registration and operational standards, ensuring authenticity in invoice and asset-backed token transactions.
- Institutional Trading: Validates that institutional entities, such as hedge funds and private equity firms, possess the necessary corporate credentials and meet regulatory requirements.
- Commodities and Precious Metals Trading: Ensures that companies dealing in tokenized commodities have passed rigorous corporate and AML checks, thereby upholding transaction integrity.
